Server Software Updates
When we talk about “server software” we mean the software running on your server, from the operating system kernel to the software packages like Nginx and PHP that run in the operating system. We do not consider scripts and web software like WordPress and its plugins server software.
Security Updates
All servers provisioned using SpinupWP are configured to automatically install security updates as soon as they are available. This reduces the likelihood that an attacker will be able to exploit a security vulnerability and is good security practice. Automatic security updates are handled by the unattended-upgrades package, which is installed and configured by SpinupWP.
Reboot Required
Often a security update will require a reboot before it can be applied (e.g. a kernel update). You may have noticed that sometimes when you SSH into your server, the welcome message says that it needs a reboot.
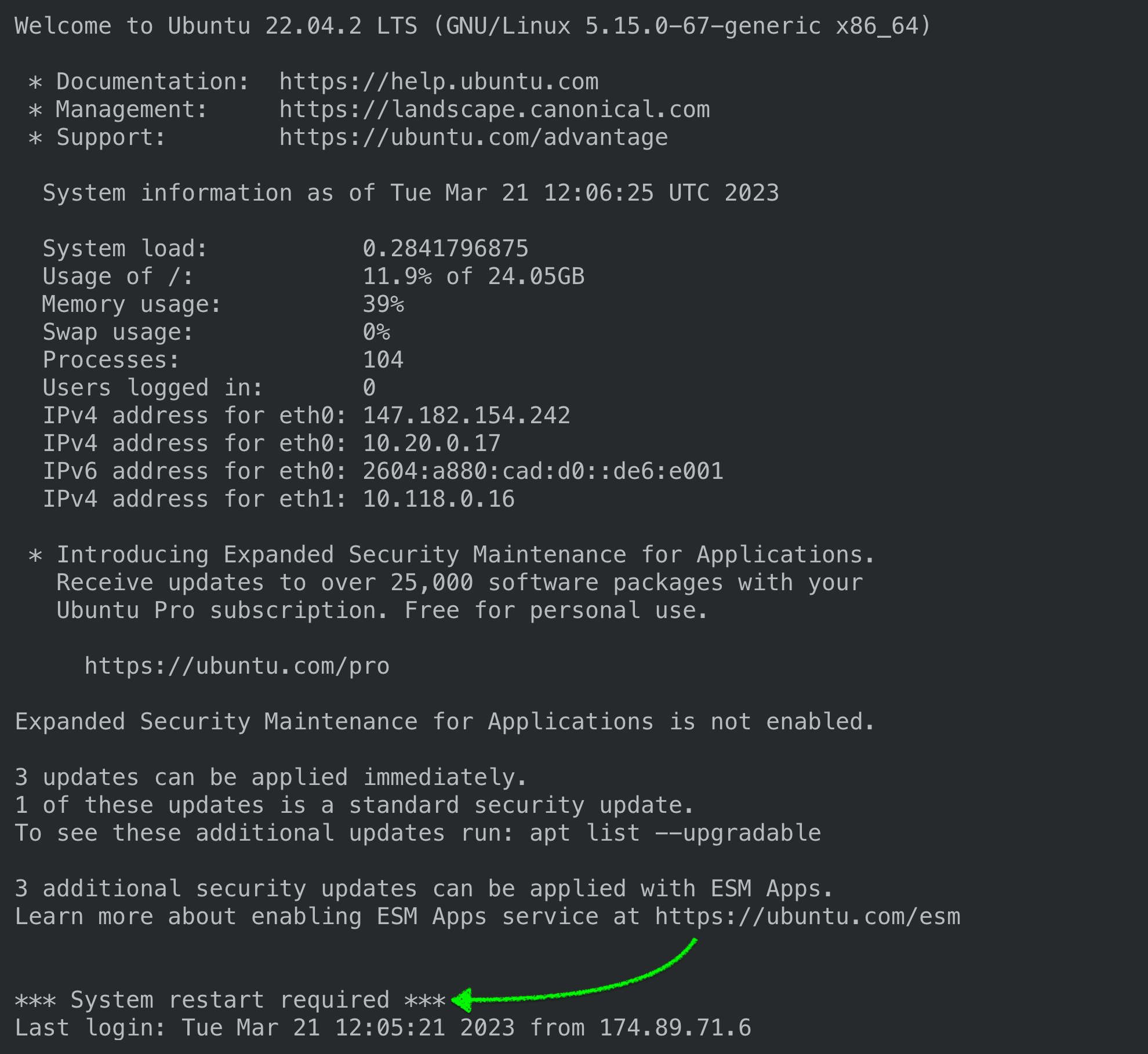
Whenever a server reboot is required for updates to take effect, SpinupWP will email you. You will also see a notice in SpinupWP and be able to reboot the server right from the dashboard.
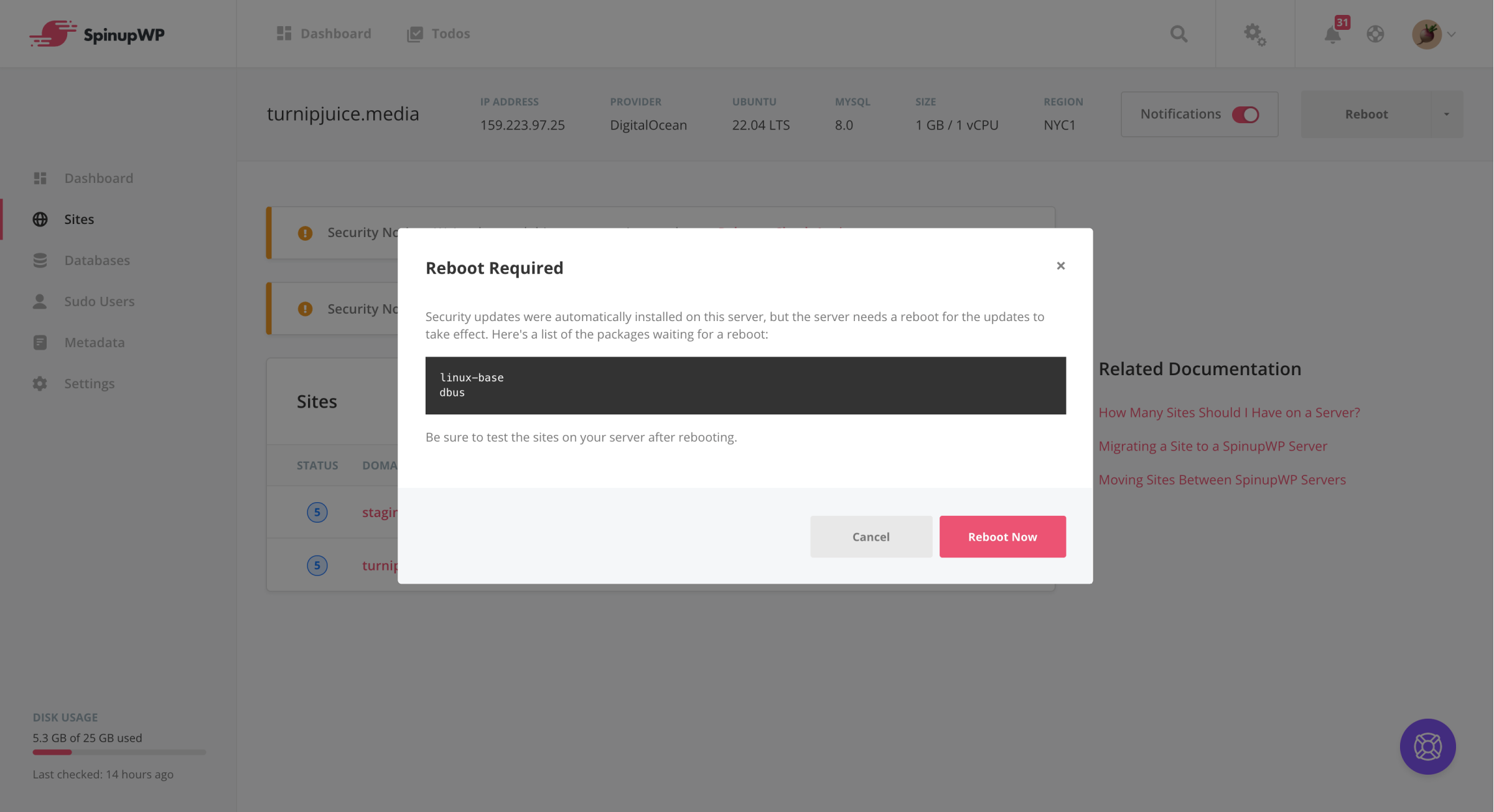
Why not reboot automatically?
It’s a risk. What happens if the server automatically reboots overnight and when it comes back, one of its sites is broken. Is someone definitely going to wake up and fix it? The answer for the majority of our customers is “No” and that’s why we don’t configure servers to reboot automatically by default.
A reboot takes less than a minute for most servers, so we recommend doing it while you’re online so that you can test your sites and handle any issues that arise. This is what we do ourselves.
During the tens-of-seconds it takes to reboot our server, any visitor requesting a page on our site experiences a connection timeout. But we believe that the risk of losing a customer during those seconds while the server is rebooting is lower than the risk of losing customers due to our site being down for hours overnight while we were asleep. We really don’t want to be woken in the night by a server issue caused by an automatic reboot.
If you simply can’t have your sites down for the tens-of-seconds it takes to reboot them during your prime time hours, we recommend performing your reboots in off-hours but still being online to test your sites after the reboot is complete. We do not recommend scheduling a reboot for a time when you’re not available afterward to test your sites and deal with any problems. Although problems after a reboot are rare, it does happen.
To minimize the number of server reboots required, you could sign up for the Canonical Livepatch Service which will apply Linux kernel security updates to your server without the need to reboot it. This service is actually free for your first three machines. This will only reduce your server reboots however, as security updates to other software packages (e.g. libsssl) will still require a reboot.
If you can’t have your server down for tens-of-seconds, you’ll need a cluster of servers where other servers will continue to serve requests while you reboot a server. SpinupWP does not currently support clusters, but it is possible to set it up manually and still control your servers with SpinupWP.
Configuring Automatic Reboot (Not Recommended)
If you don’t agree with our advice above, you can configure your server to automatically reboot after a security update where a reboot is required. Simply open the unattended-upgrades config file in your editor of choice:
nano /etc/apt/apt.conf.d/50unattended-upgrades
Locate the following line:
//Unattended-Upgrade::Automatic-Reboot "false";
Remove the double slash at the beginning and change “false” to “true”:
Unattended-Upgrade::Automatic-Reboot "true";
Save the file and your server will reboot automatically after a security update that requires a reboot.
If you’d prefer it to reboot at a certain time, you can locate the following line, remove the double slash, and edit the time:
//Unattended-Upgrade::Automatic-Reboot-Time "02:00";
Non-Security Updates
Although SpinupWP configures your server to automatically install security updates, you will be responsible for installing all other package updates. Anytime you SSH to your server, you’ll be presented with a welcome message which includes the number of outdated packages.
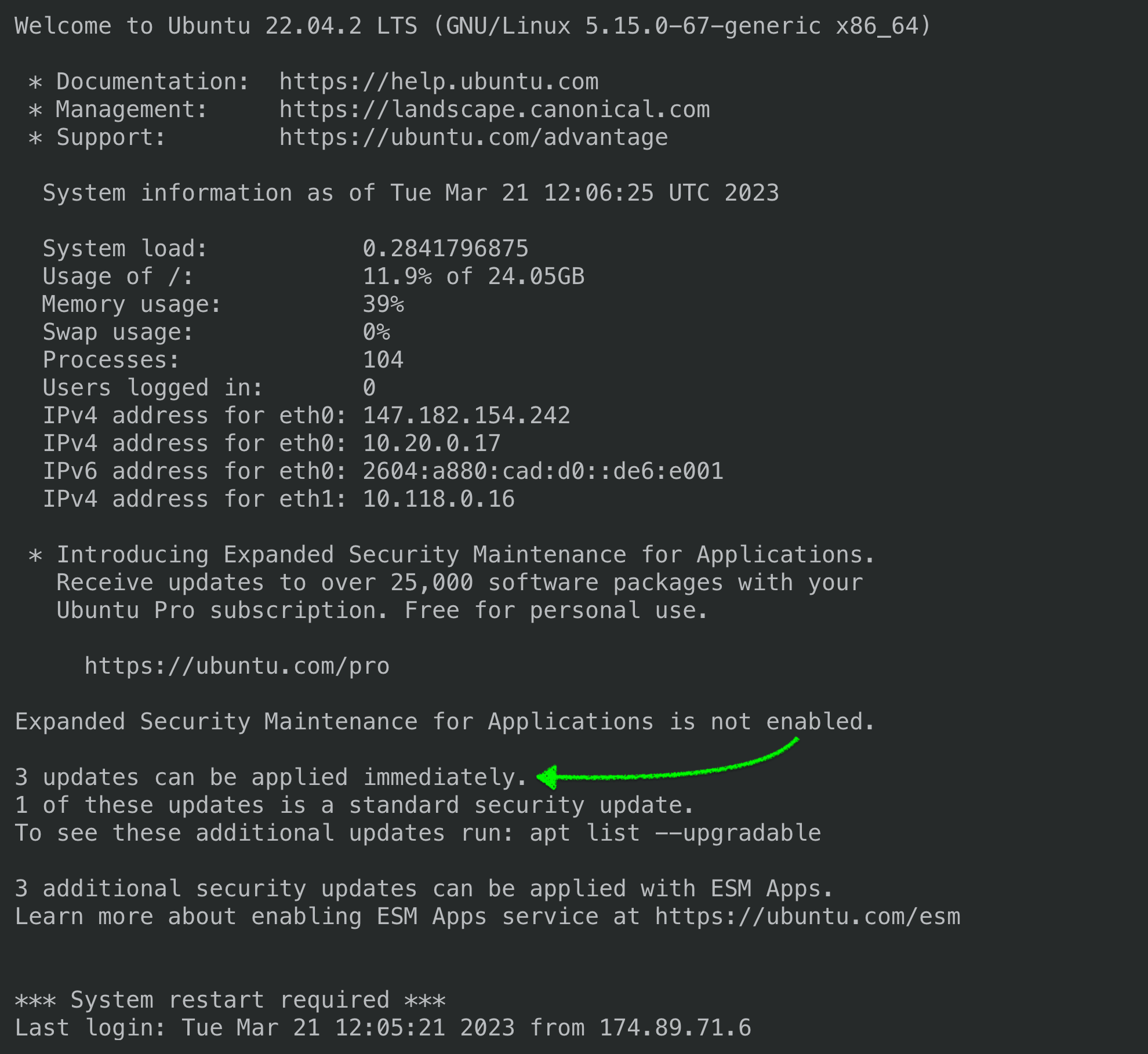
Installing Non-Security Updates
These packages can be upgraded with the following commands:
sudo apt update
sudo apt upgrade
You will need to use a Sudo User to perform these upgrades and we recommend that you perform a full server backup beforehand. Once the upgrades have been applied, be sure to test the sites on your server.
sudo apt dist-upgrade due to the potential risk that it might remove important software packages. The sudo apt upgrade command is safer as it only upgrades installed packages without removing anything. If you’re having dependency issues and searching for a solution, you may learn that sudo apt dist-upgrade could very well be that solution. However, if you do try running sudo apt dist-upgrade, please pay special attention to what packages it will remove (if any) and be sure to reinstall any critical packages afterwards.
Configuration File Notice During a Non-Security Update
During the course of running these updates, you might be presented with a notice regarding updates to a software package’s configuration file and multiple options for resolving the update. We recommend choosing the “keep your currently-installed version” option. This will ensure that the SpinupWP configurations are applied, and your server will continue to run smoothly.
Why Not Automatic Non-Security Updates?
Again it comes down to risk. For security updates, the risk of an attacker exploiting a security vulnerability is higher than the risk of a security update causing a problem with your sites. In fact, the developers who release security updates are very careful about what they change when patching a security vulnerability so as not to cause issues, so issues are very rare.
For non-security updates however, developers are far less careful. They assume that you will be paying attention when you apply these updates, test your sites, and be around to handle any issues that arise. You can probably imagine lots of ways that an update to PHP could cause problems with your sites. We’ve experienced this in the past in fact.
We recommend that you install non-security updates manually (see above), backup your server, and test your sites after the update is complete.
Configuring Automatic Non-Security Updates (Not Recommended)
If you don’t agree with our advice above, you can configure your server to automatically install non-security updates. Simply open the unattended-upgrades config file in your editor of choice:
vi /etc/apt/apt.conf.d/50unattended-upgrades
Locate the block at the top of the file similar to the following:
Unattended-Upgrade::Allowed-Origins {
"${distro_id}:${distro_codename}";
"${distro_id}:${distro_codename}-security";
"${distro_id}ESM:${distro_codename}";
// "${distro_id}:${distro_codename}-updates";
// "${distro_id}:${distro_codename}-proposed";
// "${distro_id}:${distro_codename}-backports";
};
Remove the double slash at the beginning of this line:
// "${distro_id}:${distro_codename}-updates";
Save the file and your server will automatically install non-security updates in addition to security updates.